Security
INTRODUCTION -
Cybersecurity in a distributed P2P Internet provides new challenges. A few years ago P2P networks consisted of file sharing, processor sharing and instant messaging. By adopting IPV6 routing a P2P node can extend to a device, a service, data process or storage and more.
 P2P systems can be classified as structured and unstructured. In structured P2P systems, connections among peers in the network are fixed, and peers maintain information about the resources that other or nearby peers possess. Structured P2P networks use Distributed Hash Tables (DHTs) indexing as a lookup service with (key, value) pairs. Any peer node can retrieve the value associated with a given unique key. However, this may result in higher overhead compared to unstructured P2P networks. For unstructured P2P networks, connections among peers in the network nodes use various topologies. In order to find many peers that have desired resources each node may query other nodes resources. There are many methods such as flooding, random walk, expanding-ring.
P2P systems can be classified as structured and unstructured. In structured P2P systems, connections among peers in the network are fixed, and peers maintain information about the resources that other or nearby peers possess. Structured P2P networks use Distributed Hash Tables (DHTs) indexing as a lookup service with (key, value) pairs. Any peer node can retrieve the value associated with a given unique key. However, this may result in higher overhead compared to unstructured P2P networks. For unstructured P2P networks, connections among peers in the network nodes use various topologies. In order to find many peers that have desired resources each node may query other nodes resources. There are many methods such as flooding, random walk, expanding-ring.
P2P Network Types
Three designs of unstructured P2P networks exist: centralized, hybrid, and decentralized (pure) P2P network.
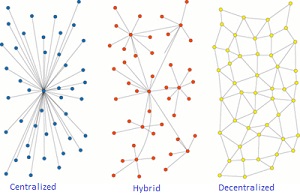 In a centralized unstructured P2P network, a central entity or node is used for indexing and bootstrapping the entire system. In contrast to the structured approach, the connection between peers in the centralized unstructured approach is not centrally determined.
In a centralized unstructured P2P network, a central entity or node is used for indexing and bootstrapping the entire system. In contrast to the structured approach, the connection between peers in the centralized unstructured approach is not centrally determined.
BitTorrent network is an example of a centralized unstructured P2P network.
The way nodes discover each other is also varied. In the Internet of Things [IOT], a method called 'graph search' is used. Here the P2P architecture has no single fixed server responsible for routing and requests among nodes. Peering nodes with IPV6 lists can act as gateways into subsets of a defined network
The decentralized (pure) unstructured P2P network is an overlay (logical routing) network. Every node has a relationship with another paired node which defines an edge. A decentralized unstructured overlay network is flat where all peers act as equals. This network type has a single routing layer. Gnutella is an example.
In order to join the network, a node first connects to one of several bootstrapping nodes which connect with one or more existing nodes (peers) in the overlay network. The peers are aware only of their neighbor nodes through their IPV6 address and port. Nodes connected with each other in the overlay network have a common virtual edge.
Queries can be passed among nodes using a variation of a flooding. A node that is interested in specific content or process sends a query to its neighbors in the overlay network. Every neighbor then forwards the query to all of its neighbor nodes. The procedure continues until the query reaches a specific depth of search limit [Time-To-Live counter].
A hybrid unstructured P2P network allows the existence of infrastructure nodes (super-nodes). This is a hierarchical overlay network that addresses the scaling problems found in pure unstructured P2P networks.
When a peer joins the network, it connects to a super-node. The peer informs its super-node about the resources it needs or may offer to others. The super-node maintains a database that maps resources to nodes, and tracks only their ressources. Similar to the centralized design, the super-node acts as a directory resource, although only to its assigned nodes.
Attack Vectors
In structured P2P networks a number of succesful attacks [Sybil, Churn, Pollution] have demonstrated security issues in P2P. Some system like Kademlia employ honeypots [unprotected nodes and super-nodes] that attract network agents or rogue nodes. The characteristics of the attack vector is analyzed and used to update the security profile in super-nodes.
The goal of malicious peers is to spread across the network using super-nodes. One method is to pollute as many routing tables as possible. Then the bad peers observe control queries by these super-nodes and are ready to hijack the network.
JIGSAW - Secure storage of data at rest
The heart of security for data at rest in both P2P and Cloud environments is in the IOTA fabric Jigsaw module. It is a critical component to manage both metadata, smart contract data and distributed ledge logic to optimize blockchain operations. Jigsaw is based on the science of byzantine fault-tolerant storage systems developed in early 2000. A Byzantine failure is the loss of a system service due to a fault in systems that require consensus from computing units or storage devices.
The original version of Jigsaw was deployed for collaboration for bioinformatics data (Proqueome). It was referred to THEN as Chromosome. In its CURRENT version it targets the secure storage of data at rest, either in a distributed IOT device network using P2P IPV6 connectivity, or in virtualized cloud computing with dedicated storage units.
Since blockchains use small data footprints, storing critical data can overload their design. Many vendors propose linking offchain operations on the data referenced by a blockchain stored URI but these have data security issues from cyberattacks. Jigsaw fixes this problem using distributed, redundant data object shredding (fragmentation)
A proprietary feature in Jigsaw is double-blind security through end-to-end encryption based on perfect forward secrecy. All communications between any point in the system (user, device, cloud resource) occur through continuous changing session keys. This is provided by the IOTA fabric InterVault module.
Distributed server modules on a remote device or a cloud instance, fragment a data object into many redundant pieces. A data object can also be fragmented multiple times for ultra security. The fragmenting module has no knowledge where fragments are eventually accepted for storage. The devices storing fragments, have no knowledge of which fragment belongs to a particular data object. This renders the stored fragments, nominally encrypted, useless to hacking.
The metadata, used to reconstruct an object, can also be shredded and stored elsewhere. What the data owner must protect is the metadata identifier to recover or destroy the fragments defining the data. Because fragments are replicated with different identifiers and distributed across devices independently of the fragmentation servers, recovering a data object is possible even if one or more devices are offline, compromised or inaccessible. How this works is shown in the following video for
Survivable E2E Secure Cloud Storage
 UbiVault Security Fabric
UbiVault Security Fabric
 Byzantine Fault Tolerance (MIT 1999)
Byzantine Fault Tolerance (MIT 1999)
 Cloud Mobile Secret Sharing
Cloud Mobile Secret Sharing
 PASIS: Storage Systems Architecture (CMU 2000)
PASIS: Storage Systems Architecture (CMU 2000)
InterVault - Secure transmission of data in motion
InterVault is a key component in the Ubivault Secure Collaboration Module, a platform to securely connect one or more parties for online interaction. It scales to hundreds of participants for secure E2E collaboration and supports:
- P2P E2E encryption
- Transcends firewalls, NAT
- Connects to Jigsaw fractal data
- Ideal for remote access to rich media eg. CAT, MRI
- Deployed in US military and government agencies
- Full range of collaborative tools:
- Stream & video share
- Chat, VoIP, video conference
- White boarding, joint interaction
- Secure repositories
- Integration to internal systems, such as EMR
Intervault uses Perfect Forward Secrecy (PFS) which is a property of cryptographic systems. It protects the content of a communication session using public/private encryption keys where the public keys are created just for the session. Unlike a master public key, a method that Microsoft Outlook uses but Google does not, if someone were to capture the master key and gain access to any private key assigned to a device or user, all prior and future communications between those parties would be compromised.
How keys are exchanged at the start of a session is critical. Intervault shared key exchange uses ECDHE_RSA which refers to elliptic curve, ephemeral Diffie-Hellman (DHE), signed by an RSA key. Ephemeral, refers to a temporary encryption key being used. Any future session uses a different shared key. The length of a session is application specific. It can be a user event accessing a service, type of service, even down to a packet or group of packets transmitted using TCP Layer 3 protocol.
Intervault employs parallel authentication server processes. Its role is to manage access to an environment, validate that a process or person is authenticated for access, and enforce permisssion controls for what the authorized entity can perform in a process. There are some drawbacks. PFS adds computational overhead that may delay a transaction. As a result, many commercial servers prohibit using PFS.
ECDHE and DHE are the cornerstones of conventional SSL secure web connection protocols. DHE is significantly slower than RSA. However, ECDHE is supported by all modern browsers. Intervault is designed to limit the computational overhead and can handle many sessions at the same time. In excess of 60,000 sessions can be maintained simultaneously per server.
|
Elliptic Curve MQV (ECMQV) MQV (Menezes-Qu-Vanstone) is an authenticated protocol for key agreement based on the Diffie-Hellman scheme. Like other authenticated Diffie-Hellman schemes, MQV provides protection against an active attacker. The protocol can be modified to work in an arbitrary finite group, and elliptic curve groups, where it is known as Elliptic Curve MQV (ECMQV). Elliptic Curve Menezes-Qu-Vanstone (ECMQV) is a key agreement performed using elliptical curves rather than traditional integers. ECMQV is authenticated, so it does not suffer Man in the Middle (MitM) attacks. However Elliptic Curve MQV leaks private session information, and a Fully Hashed MQV protocol is recommended. Authentication is necessary to avoid Man-in-the-middle attacks. Static public keys do not provide forward secrecy or key-compromise impersonation resilience. For unauthenticated Diffie-Hellman using elliptic curves, see Elliptic Curve Diffie-Hellman Exchange (ECDHE). For more technical details see [LINK]. |