Healthcare Challenges
Healthcare is a significant part of Gross National Product (GDP) at 17.3% in public and private costs.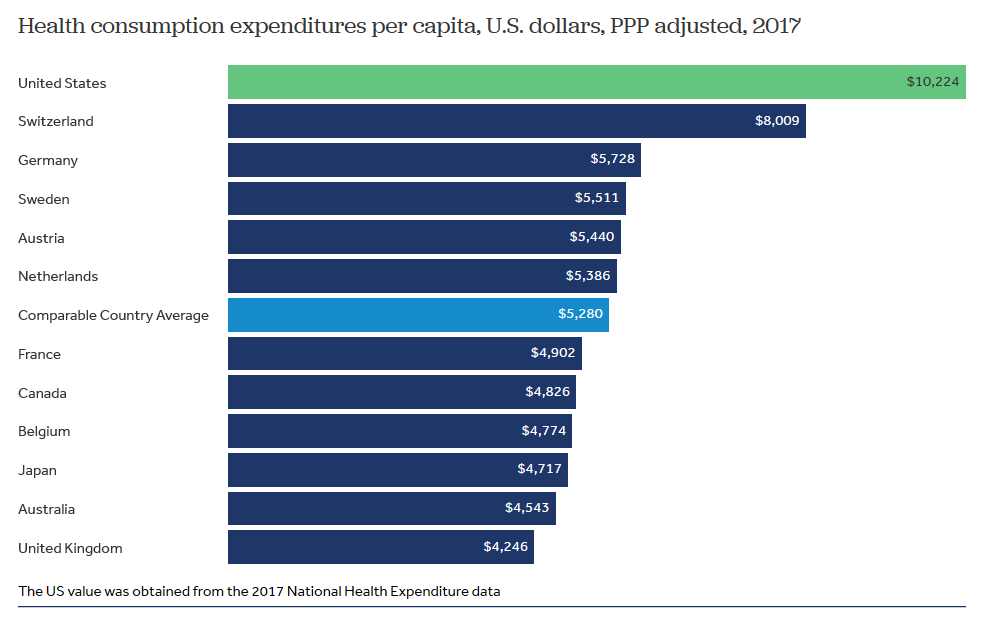
In the USA, a mix of public programs funded by federal and state governments and private insurers, is rapidly moving to digital solutions that embrace many technologies connecting subscribers with health service providers. Here are some key challenges:
- Physicians need to comply with a new CMS Value-Based Payment Modifier program, or face penalties. The Value-Based Modifier program calculates Medicare payments to physicians in group practices based on annual cost and quality measures. It is part of efforts to improve Medicare funded healthcare, but adds more regulations physicians need to monitor.
- Technologies transforming healthcare industry.
- Patient-Centered Care
- Increased Data Complexity
- International Classification of Diseases (ICD) Coding
- Data Security for Distributed Federated Networks
- Wearable Tracking Devices
- Reliance on remote diagnostics and treatment
- Financial viability of Healthcare Providers
- Defining risk in value-based health care purchasing
- Focus on population health determinants
- Improving patient treatment outcomes
- Collaboration
UbiVault is a fabric (in technical terms, a Layer 3 Protocol) that creates a secure virtual private network between all parties, using encrypted sessions that are created and destroyed upon completion of a data exchange. Our approach is based on the concept of "Perfect Forwards Secrecy" - PFS, developed for the Department of Defense and DISA certified.
| PFS uses specific key agreement protocols that gives assurances session keys will not be compromised even if the private key of a party is exposed. It protects past sessions against future compromises of secret keys or passwords. By generating a unique key for every session initiated between any party, compromising a session key will not affect any data other than that exchanged in the specific session . PFS also protects data on the transport layer of a network that uses encryption protocols such as SSL/TLS and OpenSSL. |
Connecting Resources
The Web is converging on a new architecture - decentralized resources where every thing is a node in a peer to peer (P2P) network. To date, cybersecurity has treated data protection at the edge (device, user) separate from where computing is done, on a server at a provider facility or in a cloude environment. UbiVault sees every resource as a node in a virtual network. With the advent of Software Defined Networks (SDN), each resource needs a single secure transport such as PFS to connect with other resources.
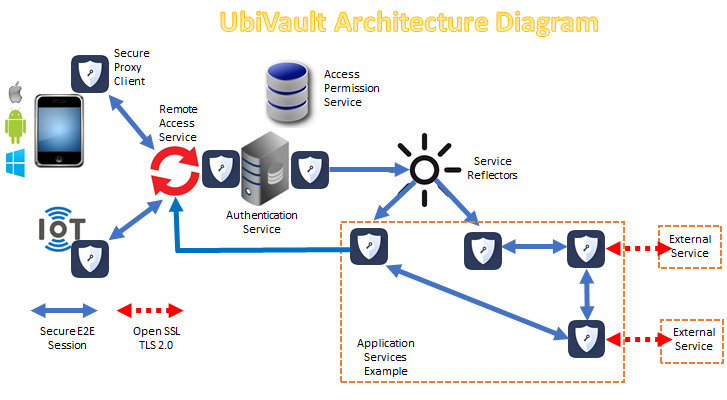
Why is PFS the right solution?
Connecting user and data sources requires penetrating firewalls, legacy systems, and data stores in a way that information is transported without knowing the content or format. This creates a lot of patchwork solutions. Using PFS simplifies how each node in the P2P network connects to other nodes. Each node has a signed unique software code that registers and is authorized to enter the network. Each node is certified and has its own public/private key pair. PFS uses this unique signature to establish onetime session keys. A data object is transported between nodes without the transport mechanism knowing the contents, encrypted or not.
How does a healthcare service use PFS?
UbiVault uses a SDN function InterVault operating on every node, whether Android/IOs, Windows or Linux. Intervault starts up and terminates every unique session. For large volume transaction systems, UbiVault provides a scalable messaging layer - Message Reflector. It allows parties exchanging data to pass it through a secure transport system - Layer 3 security protocol. Whether a hospital, clinic, pharmacy, doctor or IoT enabled remote diagnostic devices, UbiVault provide total E2E security for data in motion.
Data in motion is coupled with the UbiVault data at rest function. Using a novel sharding method, data can be stored on a decentralized storage system in the form of fragements that comprise the data object. Sensitive healthcare data can be securely stored on any system such that it is useless to unauthorized third parties. This data at rest function is referred to as Jigsaw.
Jigsaw uses a Byzantine, reduntant, fault tolerant method of storing fragments of files across disparate data storage configurations. The metadata for accessing data object fragment to recreate it is transparent to the data storage resource. It follows a "double-blind" principle: the sharded data object does not know which storage environments the object fragments are stored; the storage devices have no idea which objects the fragments belong to.
