EDGE AI

Rewarding Privacy

"I never saw an ad I didn't like since I ignore them"- Gen X
Many studies have shown that advertising is more of a distraction than a focus. Media consumers understand that advertising plays a role in paying for web services but the incessant injection of messages using latest intrusive methods leaves a bad taste. This is more prevalent on mobile devices which have limited pixel space for display and with streaming media the problem gets worse
If you follow the money trail it goes like this: A company has a marketing budget of which advertising is a part. They typically use an ad agency for print and digital media placements. The first goal is to decide where ads are viewed. This involves branded and third party websites, search engines, and now social media outlets. There are also mobile apps where ads can display.
Major ad facilitators, beyond search engines, are ad networks and exchanges. Here most targeting innovation occurs. They match publisher inventory with the most relevant ad content. Placing an ad that does not conflict with displayed content is a major goal. The publisher acts as a proxy for the viewer, assuming that its page content is why visitors are looking. Metadata on content is made available to the ad-network and, using somewhat complicated rules, drives which ad to push.
Other decision methods also play a role. Often publishers use a real-time ad auction platform that selects ads with highest cost per impression (CPM). Think of this as arbitrage. Many times publisher inventory is not fully used so ad-networks will push ads from what is called "remnant inventory". These are generic ads from advertisers looking to get maximum reach for the lowest cost - Ads mostly ignored.
What is interesting is how viewers are left out of the economic model. Yes, consumers can benefit with special offers if they join a loyalty program. Yes, they can take advantage of time sensitive offers. All these rewards are commonplace. What is not occurring is a way for viewers of ads to be rewarded for the simple act of seeing the ad, wherever it occurs.
 Imagine a product manufacturer, Samsung for example, with many product lines. They rely on the network of of ad agencies, aggregators, ad-networks. Usually a company like Samsung does not have a direct relationship with the consumers who buy their products except through warranty registrations. With the emergence of IOT protocols, Samsung now can perform remote diagnostics, software upgrades and the like to monitor product use. The Smart TV, the appliance, the smartphone, all can use the Internet to exchange data without the consumer involved. This is a fertile area for engagement and provides value to both the manufacturer and the user.
Imagine a product manufacturer, Samsung for example, with many product lines. They rely on the network of of ad agencies, aggregators, ad-networks. Usually a company like Samsung does not have a direct relationship with the consumers who buy their products except through warranty registrations. With the emergence of IOT protocols, Samsung now can perform remote diagnostics, software upgrades and the like to monitor product use. The Smart TV, the appliance, the smartphone, all can use the Internet to exchange data without the consumer involved. This is a fertile area for engagement and provides value to both the manufacturer and the user.
Once bought, the consumer has an implied, favorable relationship with the product, hence with the manufacturer. Understanding why they bought, how they use and what lifestyle they pursue is valuable. Apple is a good example of loyalty with Iphones and Macintosh computers. Establishing a relationship - lead generation - is a critical component to brand building and loyalty. This can start with an implied contract where first, advertising dollars are shared with ad viewers and second, translate into preferred customer reward programs.
Challenges
Why would a publisher agree to discounting their revenue stream so that a portion accrues to a viewer? Why would an advertiser pay for an anonymous viewer to see their ad? How does the viewer monetize this event? Is the CPM/CTC/CTR financial model outdated when we embrace emerging peer-to-peer (P2P) engagements in a Internet that moves away from a web publishing world? All good questions.
There have been previous attempts to "pay" viewers on the Web to look at advertising. Sadly, these approaches were hacked using bots to automatically visit sites mimicking an actual user. Trust is a fragile term on an untrusted Internet. But, recent technologies applied to P2P transactions provide a piece of the solution. The Internet works using a client-server model where the client is the viewer using their browser or app. Their identity is a composite of IP and device MAC addresses plus server collected identity data and passwords. Add to that browser history, cookies, parameters collected by the app, it creates a somewhat reliable identity.
Unfortunately, IP addresses are not static (using a hotspot while on the web), MAC addresses can be masked or spoofed, browser history and cookies deleted, accessing services in anonymous mode, having multiple devices that are not federated across identity (what Google is trying to fix), are all challenges to this ad revenue sharing model.
IP Challenge
One promising trend is the movement away from IPV4 of IPV6 addressing. This is how a connected device or server is recognized on the Internet backbone. The advantage is that there are way more V6 addresses available than already streched V4 addresses. As it is, IPV6 addresses can be registered in blocks by anyone and reserved for allocation to any use. Imagine Samsung having millions of IPV6 addresses to allocate for their purposes. IPV6 is limited to just over 2 billion addresses. IPV6 effectively has no limit.
We don't realize that this migration to IPV6 is well underway. Most smartphones are already enabled with their own unique address, over 2 billion in the world. [Many mobile networks are taking the step to run IPv6-only where they can, with 70-95% of their traffic using IPv6 when they do. Doing so avoids IPv4 APN costs for mobile carriers, and the cost of purchasing IPv4 address space in a network. Having a common flat address space also simplifies operations.] - Internet Society
| IPV6 Benefits: No more NAT (Network Address Translation), No more private address collisions, Better multicast and more efficient routing, True quality of service (QoS), Built-in authentication and privacy support, Flexible options and extensions, No need of DHCP |
Ad Hoc Network Challenge
In a P2P Network, there are closed network models and on-demand networks. The second describes a network that connects IPV6 enabled services regardless of their identity. Putting aside the issues of filtering related to the security permission roles of connecting disparate devices, the data traffic moves between one device and another through Internet connected pathways. If the device owner has multiple IPV6 addresses (application or device), the gateway has to recognize which path is available for connection (wireless, IP router, gateway, closed loop). this is an area of development to find the least cost, least-hop choice for connection.
In an ideal world, one sees an Internet enabled endpoint (your phone, your friend's phone) and establishes a connection regardless of path. In a client-server situation, the server takes care of the connection. In an ad hoc mesh network it is more complicated. The immediate problem is that while two addresses are locally adjacent, the path may travel through different wireless carriers, ISPs, cable providers. A 500 feet distance betweem two more devices may require multiple hops over many network points adding to latency and affecting QOS.
Ad Industry Challenge
 Is there value in rewarding viewers of ads with some form of incentive? Only if it has value to content consumption. The goal is to improve interaction in the form of a response. More responses lead to a higher level or interaction. Today, you see an ad, click on the display and are directed to another site. What you do then is between you and the advertiser, not the publisher. But what if you could determine what the viewer is all about, independent of the sites the visit? Their interests not their surfing behavior is a better target.
Is there value in rewarding viewers of ads with some form of incentive? Only if it has value to content consumption. The goal is to improve interaction in the form of a response. More responses lead to a higher level or interaction. Today, you see an ad, click on the display and are directed to another site. What you do then is between you and the advertiser, not the publisher. But what if you could determine what the viewer is all about, independent of the sites the visit? Their interests not their surfing behavior is a better target.
This is where knowing what people want, without invading their privacy, lends itself to the new Internet based on P2P connections. How this is done requires rethinking the way information is collected and analyzed in the present client-server architecture of the Internet. What is needed is a method that collects the metadata of what people do with their device.
Take the smartphone situation. Device apps, downloaded apps, browser apps are the mainstay of behavior. They describe what you do but not necessarily who you are. Additional data comes from registrations, device ownership, some banking or payment relationships, and of courses, what you do with your phone, connected or otherwise. There are information aggregators that have external data referenced by your name, address, phone number but they exist outside of the system, allowing more detailed personal data driven from demographics, psychographics, public records, and so on.
How to keep this information opaque while providing valuable information about a viewer's profile is important. One method is to utilize a proxy agent service that connects to a source without disclosing any details on the requestor, ie. the viewer, To some extent, private browsing is used today but it is still linked to the device so responder knows who requested the connection.
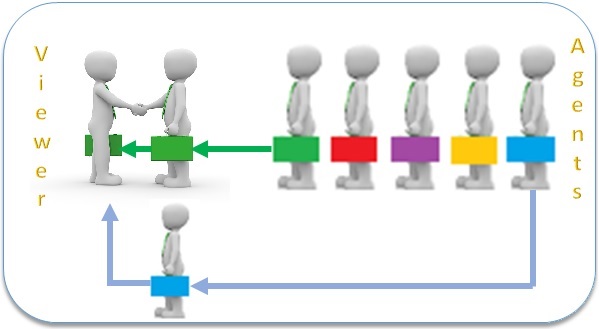 A proxy agent, using IPV6 address can connect to a source but mask where the information is sent. Such a proxy agent belongs to a very large pool of IPV6 agents from which one is randomly assigned to a requestor. At the end of a session, the agent returns to the agent pool. The requestor would ask for an agent in a new session and another agent can be assigned. The information characteristics derived from an agent by the service provider is meaningless.
A proxy agent, using IPV6 address can connect to a source but mask where the information is sent. Such a proxy agent belongs to a very large pool of IPV6 agents from which one is randomly assigned to a requestor. At the end of a session, the agent returns to the agent pool. The requestor would ask for an agent in a new session and another agent can be assigned. The information characteristics derived from an agent by the service provider is meaningless.
Since the proxy agents are stateless and randomly assigned, no provider can build a unique fingerprint of any requestor.(image below) This approach provides the first part of the solution. It keeps the viewer truly anonymous to the responder. The proxy agent is the middleman but is reused by many other viewers rendering the data useless. However, in the case of rewarding ad viewers, a smart contract can transfer value from the ad provider, through the agent into the "Ad-Wallet" of the viewer. How this is monetized is for another subject. The second part is more interesting.
Ad Profile Scoring
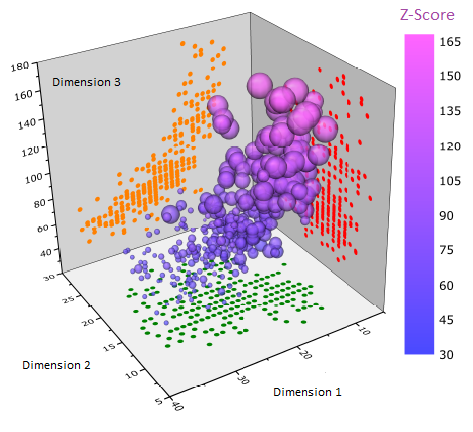
 How does the advertiser benefit? This is the second part of the solution. On the viewer side (the edge) a multidimensional profile is kept. It is used to construct a "propensity to respond" measure. Analagous to browser history, it keeps a record of engagements: what was visited, what was viewed, timestamp and other metrics. The agent sends the data to a central AI system which takes the viewer behavior anonymously as inputs into an aggregate scoring algorithm. The behavior of the viewer updates an aggregate multi-dimensional score which the agent returns to update the viewer profile.
How does the advertiser benefit? This is the second part of the solution. On the viewer side (the edge) a multidimensional profile is kept. It is used to construct a "propensity to respond" measure. Analagous to browser history, it keeps a record of engagements: what was visited, what was viewed, timestamp and other metrics. The agent sends the data to a central AI system which takes the viewer behavior anonymously as inputs into an aggregate scoring algorithm. The behavior of the viewer updates an aggregate multi-dimensional score which the agent returns to update the viewer profile.
Aggregate scores are made available to the advertising network channels as a means for targeting viewers with like interests expressed as multi-dimensional measures. One algorithm, the Z-Score [link] method, allows a universal scaling score across multiple categories. In one category, an advertisers may see the viewer in a less than desirable segment. Another score may rank higher. In this way, advertising networks can benefit from improved targeting across multiple user product categories while ensuring privacy of the viewer.